What is FHE and how Lighthouse plans to use it
Imagine a world where you can analyze sensitive data without ever decrypting it. Sounds like science fiction, right? But it's not—it's the magic of Homomorphic Encryption. This groundbreaking technology allows computations on encrypted data, preserving privacy while extracting valuable insights. Let’s dive deep into how this works and how Lighthouse Storage is venturing into this fascinating domain with Fully Homomorphic Encryption (FHE).
The Encryption Conundrum: Why Traditional Methods Aren’t Enough
Encryption is the bedrock of data security, ensuring that your sensitive information stays hidden from prying eyes. But here’s the catch: traditional encryption only protects data when it’s at rest (stored) or in transit (being sent somewhere). As soon as you need to process or analyze that data, you have to decrypt it, exposing it to potential risks. Imagine handing over the keys to your treasure chest just because you need someone to count the gold inside. It’s a vulnerability that businesses, especially those handling sensitive information, have had to live with—until now. These traditional encryption methods, while robust, fall short when applied to the unique challenges of blockchain and AI. Let's break down why:
- Vulnerability During Data Processing: Traditional encryption methods protect data at rest (when stored) and in transit (when being transferred). However, as soon as you need to process or analyze the data—whether it's running computations on it or training AI models—you have to decrypt it. This decryption process exposes the data to potential breaches. In a blockchain environment, where transparency and immutability are key, this exposure is especially problematic. The moment the data is decrypted, it's vulnerable to attacks from within the network, undermining the very security blockchain aims to provide.
- Incompatibility with Decentralized Systems: Blockchains are decentralized, meaning data is stored and processed across multiple nodes. Traditional encryption methods, designed for centralized systems, struggle to adapt to this environment. When data is decrypted for processing on a blockchain, it becomes visible to all nodes, increasing the risk of unauthorized access. This is particularly concerning when dealing with sensitive datasets, such as financial information or personal data, where privacy is paramount.
- Challenges in Secure AI Model Training: Training AI models requires vast amounts of data, often involving personal or proprietary information. Traditional encryption methods necessitate decrypting this data during training, leaving it exposed. On blockchain, this exposure is even more dangerous due to the distributed nature of the network. If any node in the network is compromised, the entire dataset could be at risk. This makes it difficult to ensure the privacy and security of the data used in AI training.
- Lack of Scalability: Traditional encryption methods were not designed with the scale of blockchain in mind. As the amount of data stored and processed on the blockchain increases, so does the risk. Decrypting and re-encrypting large volumes of data can be time-consuming and resource-intensive, slowing down the entire system. This lack of scalability is a significant hurdle for blockchain applications that require the secure handling of large datasets, such as AI training.
Homomorphic Encryption Keeps Secrets While Doing the Math. But How?
Imagine needing to perform complex calculations on your most sensitive data—think customer financial records, medical histories, or proprietary algorithms—without ever having to unlock it from its secure vault. That's the promise of Homomorphic Encryption (HE). Homomorphic Encryption allows you to perform computations directly on encrypted data, yielding results that are identical to what you'd get if the data were decrypted. It's as if you hired a vault master who could count your gold, weigh it, and even divide it into piles, all without ever opening the chest. The gold stays safe inside, untouched and unseen, but you still get the precise outcome you need.
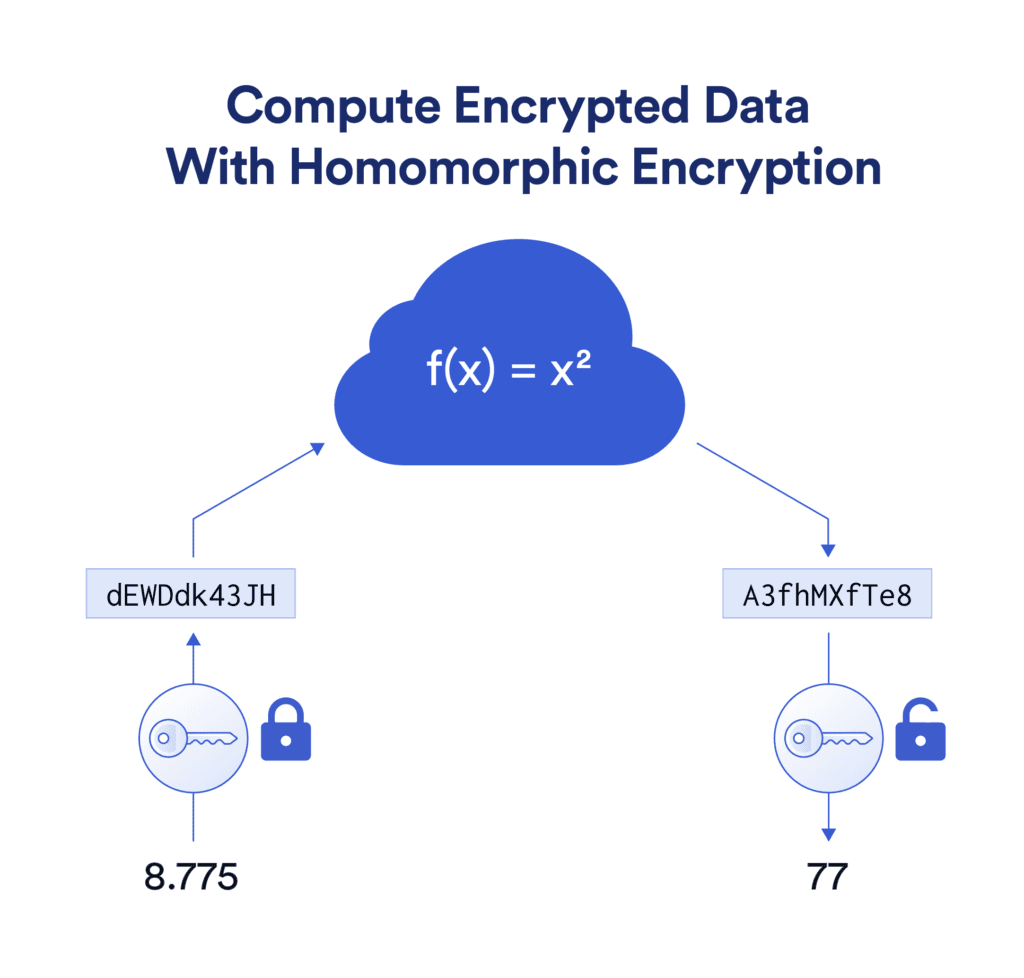
How is it different?
While traditional encryption methods lock up your data and throw away the key until you need to use it, Homomorphic Encryption keeps the key safely hidden, even during processing. But not all Homomorphic Encryption is created equal. There are mainly 3 forms of HE, each with its own capabilities:
- Partial Homomorphic Encryption (PHE): Allows only a specific type of operation (like addition or multiplication) on encrypted data, but not both.
- Somewhat Homomorphic Encryption (SHE): Supports a limited number of operations before it needs to be decrypted. These methods, while useful in certain contexts, are still limited. They can't handle the full complexity of operations required by modern applications like machine learning, where data often needs to undergo numerous and varied computations. But Fully Homomorphic Encryption (FHE) allows for any type of computation on encrypted data, no matter how complex. Whether you're running machine learning algorithms, conducting data analytics, or even facilitating secure electronic voting, FHE can process it all without ever exposing the underlying data.
What Makes FHE so EPIC?
-
End-to-End Security in AI: AI model training often requires vast amounts of sensitive data. With FHE, you can train these models directly on encrypted datasets. The data never needs to be decrypted, ensuring that personal information, trade secrets, or proprietary algorithms are never exposed, even during intensive computational processes.
-
Complex Computations, Zero Exposure: FHE enables you to perform intricate operations, like training AI models or running advanced analytics, without decrypting the data. This is especially critical in blockchain applications, where data is distributed across multiple nodes and must remain secure at all times.
-
Enabling Trustless Computation: One of the core principles of blockchain is the concept of trustless transactions—where participants don’t need to trust one another because the system itself guarantees security. FHE takes this a step further by enabling trustless computation. Even in decentralized environments where nodes may not fully trust each other, FHE ensures that data can be processed without being exposed, preserving the integrity and confidentiality of the information.
-
Future-Proofing Against Quantum Threats: As quantum computing advances, the security of traditional encryption methods is increasingly at risk. FHE, with its advanced cryptographic techniques, offers a layer of protection that is more resistant to these emerging threats. By allowing computations on encrypted data, FHE reduces the risk of exposure, even in a quantum world.
-
Privacy-Preserving Data Sharing: FHE makes it possible to share encrypted data with third parties for processing without ever revealing the underlying information. This is particularly valuable in industries like finance, where institutions need to collaborate on data without compromising privacy.
Are There Any Real-World Applications of FHE?
Well, there is a whole FHE ecosystem out there. Fully Homomorphic Encryption (FHE) is quickly becoming a cornerstone of privacy-focused innovations, and a vibrant ecosystem is emerging around this technology.
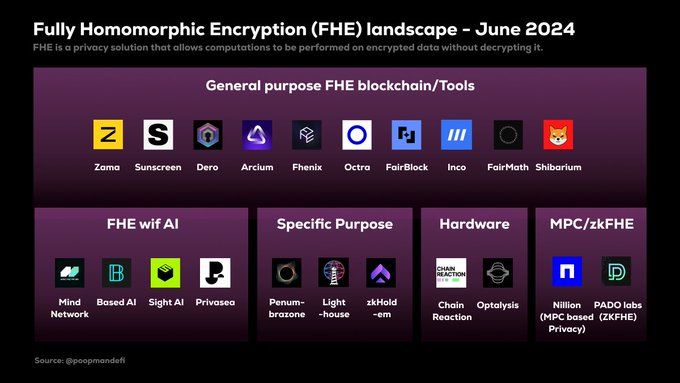
Take a closer look at some of the key players and what they’re bringing to the table:
- Zama: With their TFHE and fhEVM, Zama is making FHE work seamlessly with Ethereum, enabling private on-chain computations and smart contracts.
- Fhenix: Known for their FHE Layer 2 solutions, Fhenix is developing specialized coprocessors to accelerate FHE computations.
- Privasea: At the intersection of AI and FHE, Privasea is creating privacy-preserving AI models that keep sensitive data secure.
- Octra: Building an FHE-focused Layer 1 blockchain, Octra is laying the groundwork for a privacy-first decentralized ecosystem.
- IncoNetwork: Another player in the FHE Layer 1 blockchain space, IncoNetwork is developing tools to make FHE more practical and scalable.
- FairBlock: Specializing in modular FHE solutions, FairBlock is crafting tools that can be easily integrated into existing systems to enhance privacy.
- MindNetwork: Exploring decentralized AI with FHE, MindNetwork is pushing the boundaries of what’s possible in secure machine learning.
- SunscreenTech: Known for their FHE compilers, SunscreenTech is making it easier for developers to implement FHE in their applications.
- zkHoldem: Using FHE to make on-chain gambling secure, zkHoldem is blending privacy with entertainment on blockchain platforms. These companies are not just building tools—they’re crafting the future of privacy in a decentralized world. The FHE ecosystem is rapidly expanding, with innovations in general-purpose FHE blockchains, hardware acceleration, and specialized applications like private voting and confidential ERC20 tokens.
Why Should You Care About Homomorphic Encryption? (No, Really)
Homomorphic Encryption isn't just a technical marvel—it's a transformative technology with real-world implications that touch every aspect of data security and privacy. Here's why it matters to you:
- Enhanced Privacy: Your Data Stays Safe, Always Traditional encryption methods are effective at keeping your data safe when it's stored (at rest) or being transmitted (in transit). However, the moment you need to use that data, whether for analysis, processing, or anything else, it must be decrypted, exposing it to potential risks. With Homomorphic Encryption, your data remains encrypted throughout its entire lifecycle, including during computation. This means that even while performing operations on your data, it stays protected, drastically reducing the risk of exposure. For instance, if you're handling sensitive financial information or personal medical records, Homomorphic Encryption ensures that this data is never exposed, not even to those performing the computations. This enhanced privacy is crucial in an era where data breaches and privacy violations are increasingly common.
- Secure Collaboration: Trust Without Compromise Sharing data with third parties, whether cloud providers, business partners, or research institutions, has always been a double-edged sword. On one hand, collaboration is necessary for innovation and efficiency. On the other, sharing data often means compromising its security, as it typically requires decryption at some stage. Homomorphic Encryption changes the game by allowing you to share encrypted data that can still be processed by the third party. The cloud provider or partner can perform the necessary computations on the data without ever seeing the raw, unencrypted information. This secure collaboration means that you can take advantage of cloud computing's scalability and processing power without sacrificing privacy. Imagine a scenario where multiple organizations need to collaborate on a sensitive research project. With Homomorphic Encryption, they can share encrypted data and run joint analyses without ever exposing their confidential data to one another. This fosters collaboration while maintaining strict privacy controls.
- Unlocking AI & ML Potential using FHE Artificial Intelligence (AI) and Machine Learning (ML) thrive on data, but when that data is sensitive, like patient records, financial transactions, or proprietary algorithms, there's always a tension between using the data and keeping it secure. Homomorphic Encryption resolves this tension by allowing AI and ML models to be trained on encrypted datasets. This means you can unlock the full potential of AI and ML without ever exposing sensitive information. For instance, a healthcare provider could use Homomorphic Encryption to analyze encrypted patient data for predictive analytics or personalized treatment plans, ensuring that patient privacy is never compromised. Moreover, companies can collaborate on AI projects by sharing encrypted data and models, allowing them to innovate together without risking data breaches. This capability is especially crucial in sectors like finance, healthcare, and cybersecurity, where the integrity and confidentiality of data are paramount.
How Does Lighthouse Come Into This?
Now, here’s where it gets even more interesting. We at Lighthouse Storage are exploring the integration of Fully Homomorphic Encryption into its platform. But why? We aim to enable our users to store and process large encrypted datasets securely, making it perfect for AI startups, financial institutions, and healthcare organizations.
By leveraging FHE, Lighthouse can offer:
-
Encrypted Data Processing: Allowing computations on stored data without ever decrypting it, ensuring that privacy is never compromised.
-
Secure Sharing: Collaborate across untrusted domains without the risk of data exposure.
-
Regulatory Adherence: Meet the highest standards of data privacy laws by keeping sensitive data encrypted, even during processing.
But Why Isn’t Homomorphic Encryption Everywhere Yet?
If Homomorphic Encryption (HE) is so powerful, why isn’t it the standard everywhere? The short answer: it’s complicated. Despite its incredible potential, there are several significant challenges that have prevented HE—especially Fully Homomorphic Encryption (FHE)—from becoming ubiquitous.
-
Computational Cost: FHE is computationally intensive. It requires vast amounts of processing power and time, making it slower and more expensive compared to traditional encryption methods. This high computational cost has been a significant barrier to widespread adoption, particularly for applications that require real-time processing.
-
Noise Accumulation: One of the technical challenges with HE is the accumulation of noise during computations. Each operation on encrypted data introduces a small amount of noise. Over time, this noise can build up, potentially corrupting the results and making the data unusable. While bootstrapping techniques can clean up this noise, they add additional computational overhead, further slowing down the process.
-
Complexity: Implementing and maintaining HE systems is not straightforward. The mathematics behind HE is complex, requiring specialized knowledge to implement effectively. This complexity increases the risk of errors, making it more challenging to develop robust and secure HE solutions.
-
Limited Practical Implementations: Although FHE can theoretically support any computation on encrypted data, practical implementations have been limited to simpler operations or require substantial simplifications. This limitation means that many use cases are still beyond the reach of current FHE technology.
Remedies and Ongoing Research
Despite these challenges, the field of HE is rapidly advancing, with researchers and innovators working on several promising solutions:
-
Trusted Execution Environments (TEEs): TEEs provide a secure area within a processor where computations can be performed safely, even in potentially compromised environments. By combining HE with TEEs, it’s possible to offload some of the computational burden while maintaining strong security guarantees.
-
Improved Algorithms: Advances in HE algorithms, such as more efficient noise management techniques and optimized encryption schemes, are helping to reduce the computational overhead. These improvements are making HE more practical for a broader range of applications.
-
Hardware Acceleration: Specialized hardware, such as FHE-specific coprocessors or GPUs, can significantly speed up HE operations. Companies like Optalysys and Cysic are developing hardware solutions designed to accelerate FHE computations, making them more feasible for real-world applications.
Noise Reduction Techniques: Researchers are exploring new methods to manage and reduce noise accumulation in HE systems. Techniques like TFHE, CKKS, and BGV are being developed to strike a balance between noise tolerance and computational efficiency, making HE more reliable and scalable.
- Layered HE Architectures: By using a combination of different HE types, such as PHE, SHE, and FHE, it’s possible to create layered encryption schemes that optimize performance for specific use cases. For instance, PHE or SHE might be used for less sensitive operations, with FHE reserved for critical computations.
Does FHE Seem Interesting To You?
You will absolutely love this playlist of FHE Summit 2024 by FHEOnChain. https://youtube.com/playlist?list=PLeyFSoYRt-Wmp9w8THT64Bg3XOl1ZEw3O&si=4C3cb_AfuHxEgmqJ
Final Thoughts
While Homomorphic Encryption isn’t yet a silver bullet for all privacy challenges, the progress being made is encouraging. As computational costs decrease and noise management improves, we can expect HE, especially FHE to play an increasingly vital role in securing sensitive data. The integration of HE with technologies like TEEs and hardware acceleration will further enhance its practicality, paving the way for broader adoption across industries. The future of data privacy may well be homomorphic, and as the technology continues to evolve, the dream of secure, private computations without compromising performance is steadily becoming a reality. The future of privacy is bright, and with innovators like Lighthouse leading the charge, we’re well on our way to a world where data is always protected, even when it’s in use.
Our Blogs
Read our latest blog
Shivang Kamboj
Lighthouse Monthly Update – October 2025
Nandit Mehra
Lighthouse Monthly Update – August 2025
Nandit Mehra
Lighthouse July 2025 Update – Real Infra, Real Recognition, Real Builders
Nandit Mehra
Lighthouse Monthly Update – June 2025 🚀
Parv
Getting Started with Threshold Cryptography
Parv
Permanent Storage Powered by Lighthouse
Parv
What is IPFS Pinning & A Complete Guide with Lighthouse
Nandit Mehra
Lighthouse Monthly Update – May 2025
Nandit Mehra
Lighthouse Monthly Update – April 2025
Nandit Mehra
Lighthouse Monthly Update – February 2025
Nandit Mehra
Lighthouse Monthly Update – January 2025
Nandit Mehra
The Role of Blockchain in AI & Data Storage: A Decentralized Future for Technology
Nandit Mehra
November at Lighthouse: Milestones & Innovations
Nandit Mehra
October at Lighthouse: Milestones & Innovations
Nandit Mehra
September at Lighthouse: Milestones & Innovations
Nandit Mehra
August at Lighthouse: Milestones & Innovations
Nandit Mehra
AI Meets Blockchain: Beyond the Hype & Into the Future
Nandit Mehra
What is FHE and how Lighthouse plans to use it
Nandit Mehra
Discover How the Endowment Pool Makes Your Data Immortal
BananaCircle
Web2 Storage Challenges Versus Web3 Solutions Ft. Lighthouse
Ishika Rathi
On-Chain Encryption: Security Unveiled
Ishika Rathi
NFT Storage Strategies
Ishika Rathi
Exploring Web3 Advancements in Storage Solutions
Ishika Rathi
Eternalizing Data: A Permanent storage
Ishika Rathi
Revolutionizing Permanence in Data Storage
Ishika Rathi
Decentralized Excellence: Elevating Data Storage with Lighthouse
Ishika Rathi
Navigating Permanent Storage: Harnessing the Power of Filecoin and IPFS
Ishika Rathi
Unveiling the Mechanics of Perpetual Storage
Ishika Rathi
Decentralized Storage: A Smarter, Safer, and Cheaper Way to Manage Your Data
Ishika Rathi
Lighthouse: Secure Web3 Storage for Your AI Data
Ishika Rathi
Understanding How web3 storage Operates
Ishika Rathi
Web3 Storage: IPFS and Filecoin Guide
Aryaman Raj
Passkey Demo App with WebAuthn and Ethereum
Aryaman Raj
Secure File Sharing using Lighthouse SDK: A Step-by-Step Guide
Aryaman Raj, Nandit Mehra
Time Lock Encryption using Lighthouse Access Control
Aryaman Raj
A Comprehensive Guide to Publishing and Updating Content with Lighthouse IPNS
Aryaman Raj
Getting Started with Lighthouse Python SDK
Ravish Sharma
Creating a Pay-to-View Model Using Lighthouse Storage
Nandit Mehra
Decentralized storage for the Ocean Protocol
Lighthouse
How To Migrate Your Files To Lighthouse
Nandit Mehra
Encryption and Access Control for Web3 using Lighthouse